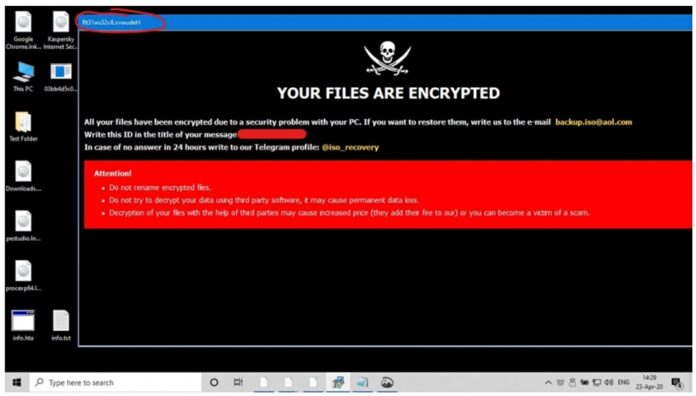
Humans are often the weakest link in a corporate network and the entry point for ransomware attackers, a factoid that underscores the necessity for persistent vigilance against this growing cyber threat.
A stark reminder of this was today presented by cloud storage provider Backblaze in its 2023 Complete Guide to Ransomware report. The latest edition of this annual report states:
“This year’s most important update has been the rise of generative AI for increasingly sophisticated, automated phishing attempts… Text generated by models like ChatGPT help cybercriminals create very personalized messages that are more likely to have the desired effect of getting a target to click a malicious link or download a malicious payload.”
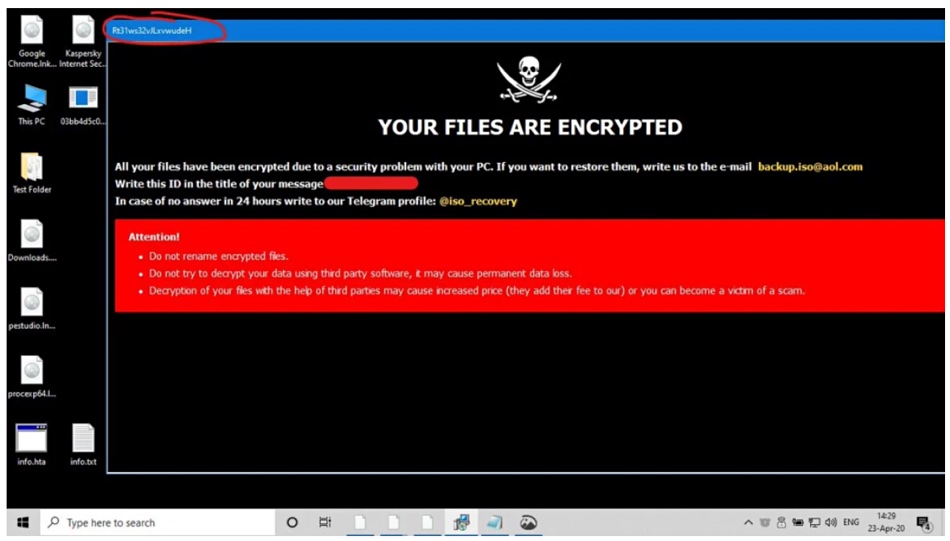
Traditionally, phishing messages were relatively easy to identify, often featuring spelling errors, grammatical mistakes, and awkwardly constructed sentences. With the aid of software like ChatGPT, however, “criminals can enter a prompt to quickly receive error-free, well-written, and convincing copy that can be immediately used to target victims.”
The report provides a comprehensive review of ransomware’s prevalence, attack vectors, the sequence of events during an attack, and the necessary steps for responding to an attack. It stops short of suggesting foolproof methods to prevent attacks from breaching IT infrastructure, as no solution that is 100 percent reliable exists.
The best measures involve proactive steps: ensuring robust IT user education and having an efficient recovery system in place to restore encrypted files from uncorrupted backups. If sensitive data has been exfiltrated, however, the options are limited.
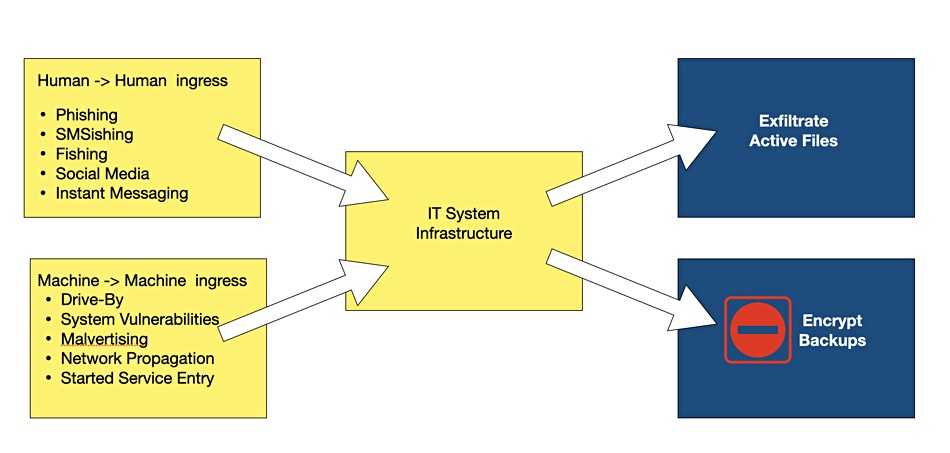
Malware attack vectors can be either human or machine-mediated, each designed to deliver malware into IT systems, encrypting files or copying them for transmission to attacker HQ. Victims someimes pay a ransom, often in cryptocurrency, to decrypt their files or prevent widespread distribution.
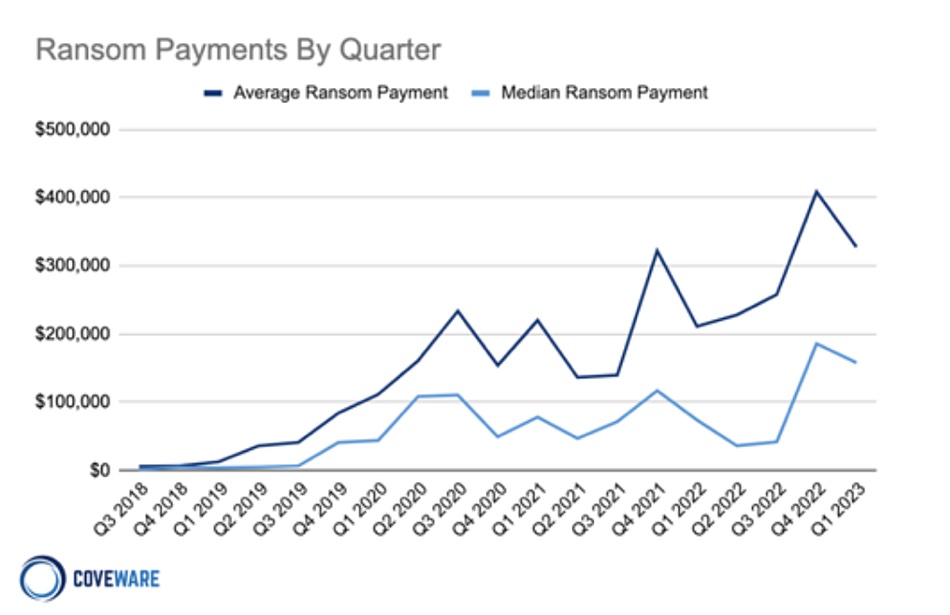
The caveat, of course, is that dealing with cybercriminals doesn’t guarantee a successful outcome even after paying a ransom. Backblaze’s report warns: “Paying the ransom only encourages attackers to strike other businesses or individuals like you. Paying the ransom not only fosters a criminal environment but also leads to civil penalties – and you might not even get your data back.”
Victims should report attacks to the appropriate authorities. If data has been encrypted, it’s recommended to recover it using clean backups. Increased vigilance in protecting sensitive data and transparent communication with potentially impacted parties is advised.
Preventing malware infiltration into systems requires a comprehensive approach. Backblaze recommends several protective measures such as to “restrict write permissions on file servers as much as possible.” In addition to this, we would suggest restricting file movement permissions to prevent sensitive data from leaving the boundaries of your IT system.
Modern IT security strategies increasingly adopt a zero-trust model – no person, device, or service requesting data access is automatically trusted, but must be validated every time, even for repeat requests. This principle should also extend to file egress destination devices, given the risk of trusted services unintentionally transferring sensitive files to an unsecured location, as in the case of Fortra or MOVEit.
The 2023 Complete Guide to Ransomware report is accessible on Backblaze’s website through its blog page.