Data loss prevention (DLP) measures are supposed to prevent data loss yet they did nothing to stop the large scale file exfiltration caused by malware that disrupted the widely used Fortra and MOVEit file transfer services. Code42 CEO Joe Payne claims this is because DLP has a blind spot and cannot see the attacks. New approaches are needed, he thinks.
Blocks and Files: Could existing DLP measures have foiled the Fortra and MOVEit file exfiltration attacks?

Joe Payne: Because this was a SQL injection attack into MOVEit code and the hackers were accessing the files through MOVEit servers, traditional DLP solutions would not have been able to see or stop those attacks. In fact, 76 percent of organizations have suffered a data breach despite having a DLP solution in place.
Modern data protection solutions, like Code42 Incydr, do see and help stop exfiltration caused by malware when a user is compromised on the company’s endpoint or on their corporate OneDrive account, for example. Malware attack red flags go up when clients see large volumes of files moving to untrusted destinations.
Blocks and Files: How does DLP technology work? Does it rely on a list of don’t-export files and a separate list of acceptable file transfer destinations?
Joe Payne: Traditional DLP tends to focus on the content itself – relying on labeling and tagging data to determine what employees can and can’t do with it. There are several problems with the traditional DLP approach, though.
First, accurately labeling all data at scale is practically impossible because of the huge volume of digital products that employees are working with; and because most traditional DLP tools only oversee data that’s been labeled “confidential,” they can miss risky activities.
Others analyze content to find patterns, like recognition of credit card number strings, which insiders can easily obfuscate by adding an extra number. When faced with these systems, users who plan to exfiltrate a file can easily bypass their organization’s DLP system by simply not labeling it as confidential or by changing the recognizable pattern.
Modern data protection solutions created for structured and unstructured data, on the other hand, focus on user behaviors and data destinations, rather than content. They aim to secure sensitive data across endpoints and in the cloud, quickly detecting when data goes to untrusted locations.
Blocks and Files: Could you see DLP suppliers offer guarantees like the anti-ransomware guarantees of some backup vendors?
Joe Payne: Because they take a very basic approach to content inspection, traditional DLP misses a lot of risky activities. So a guarantee like this would put a lot of DLP suppliers with an outdated approach out of business.
Blocks and Files: Do we need an air traffic control-like facility for file transfer?
Joe Payne: This is a great analogy. Companies need solutions that allow traffic to flow – allowing employees to collaborate. Solutions that constantly throw up barricades or only monitor some traffic are not only ineffective when it comes to security, but also hamper efficiency and hinder the innovative collaboration that today’s businesses rely on for a competitive edge.
At Code42, we believe in securing the collaboration culture – meaning that we automate response to everyday mistakes via microlearning modules for accidental and non-malicious risk, block the unacceptable risks, and thus free up security teams’ time to investigate truly problematic activity.
Comment
This statistic that 76 percent of organizations have suffered a data breach despite having a DLP solution in place is noteworthy. A chart from a Code42-commissioned Ponemon report shows that in 2021, only 19 percent of data breaches were caused by a third-party mishap.
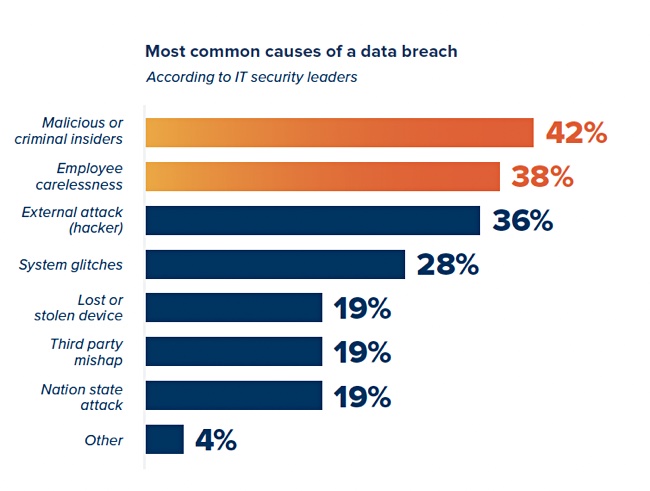
That description, third-party mishap, is exactly what happened in the Fortra and MOVEit data breaches. Even Code42’s expanded data loss prevention focus on insider behaviors would not have prevented them because the Fortra and MOVEit code was effectively treated as if it were a privileged outsider by each customer organization.
It seems to us that relying on third parties like Fortra and MOVEit to prevent data breaches through their software and services is not enough. We need some way for vendors to be able to inspect such privileged outsider-initiated file movements and prevent them happening, if they are unwarranted.








