Hewlett Packard Enterprise says its Zerto data protection can offer real-time detection of ransomware encryption across diverse data types, within the VMware environment, and can recover data to the point just before an attack.
Update. Zerto ransomware detector only works in VMware environment. 31 July 2026.
The newly released Zerto 10 employs a Shannon entropy detector, the details of which are elaborated in a blog by HPE Senior Distinguished Technologist, Dimitris Krekoukias. He writes: “A modern ransomware detection mechanism needs to be able to deal both with legitimate host-level activity, plus modern ransomware, dynamically, without relying on fixed thresholds and with no assumptions regarding data types.”
HPE’s Zerto provides continuous data protection and disaster recovery. A launch video features Deepak Verma, VP of Product at Zerto, explaining: “What we’re embedding in Zerto 10 is a new detector, a set of algorithms that detect encryption at the block level. So, regardless of the operating system that’s being used, being able to detect if a singular block of data is encrypted. We’re doing this in batches.”
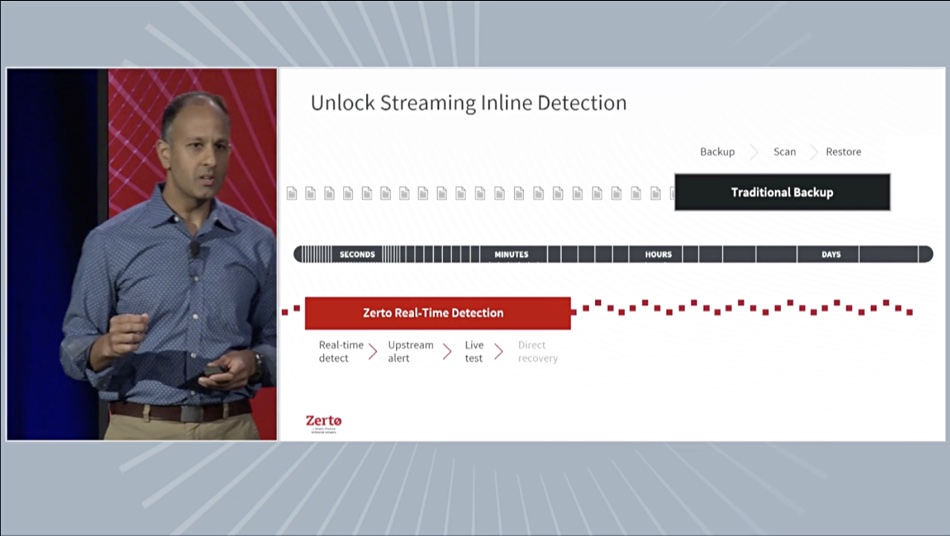
Zerto’s Virtual Replication Appliance (VRA), when running in a host server, duplicates write data headed for storage and replicates it to a target HPE/Zerto system. The copied data is analyzed outside of the production data stream to avoid production delays. An inline ransomware detector is embedded at the VRA replication target level to analyze the copied data blocks.
However, Krekoukias states that identifying ransomware-induced encryption can be challenging due to legitimate encryption of data by IT systems and the variety of data types involved. Traditional ransomware detection methods involve searching for high Shannon entropy levels in a set of data blocks, with unexpected shifts indicating abnormal activity. [More details here.] This method, though, has limitations due to the fixed thresholds it relies upon.
The fixed thresholds, Krekoukias explains, can be problematic as they differ depending on data types, data compression, and tricks like encoding data using base64. This results in encrypted data appearing to have less entropy and could hinder the effectiveness of fixed threshold detection systems.
By contrast, he claims, Zerto 10’s detector produces more accurate results because of its dynamic data type awareness. Krekoukias writes: “To further increase accuracy, the solution trains itself. That training is automatically done per stream, which further enhances accuracy.”
Once ransomware encryption is detected, the encrypting process can be halted and the affected data can be recovered up until the point the ransomware attack was detected. Krekoukias says: “This can enable things like identifying what servers/files started first to be encrypted, and then rolling back to the last known write operation before ransomware started encrypting – which allows businesses to recover and quarantine the best possible way, with the least amount of risk and disruption.”
He told us: “It works in VMware environments. ”
Bootnote
IBM has also utilized Shannon Entropy in its Storage Virtualize ransomware detection facility.








