CTERA’s latest software claims to be able to detect ransomware attacks against the file system as they happen and stop them in their tracks.
The idea is to monitor write activity in CTERA’s global file system using ML models to detect anomalous behavior, such as a spike in encrypted writes. CTERA uses its global filesystem to provide file access to distributed users using edge filers (or caches). As the edge users create new files and versions of files, these are synced to the global file system. CTERA’s software creates read-only snapshots of the files every 30 seconds and retains them in read-only form for a policy-set retention period.

CTERA CEO Oded Nagel said that to protect against ransomware: “Organizations need to concentrate their defense around their file storage and backup systems, which are the primary target of any attacker. By integrating this capability into our file system, we are providing integrated cyber resilient storage without relying on any third-party products and without impacting performance.”
Ransomware protection has become table stakes for data protection suppliers, distributed file systems, file system orchestration suppliers, and others, with real-time attack detection the holy grail. Nebulon, for example, has set up its Tripline attack detection facility with ML analysis of block-level IO. Sysdig uses the Falco threat detection engine to protect containerized app environments, again using ML.
Ransom Protect can detect attacks seconds after they start. A dashboard facility logs the attack and alerts admin staff who can then initiate recovery.
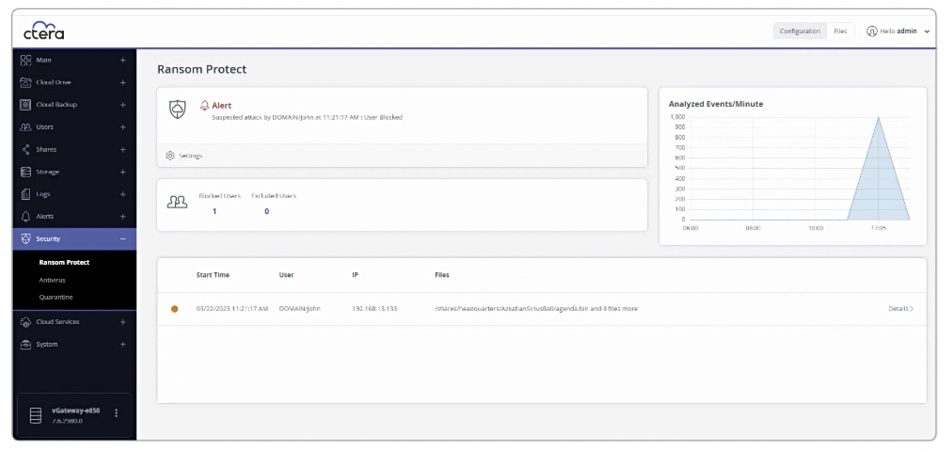
CTERA relies on its immutable snapshots for recovery. It says they are held with a virtual airgap between them and the file system. Once an attack has been detected, the offending user account is blocked. Files can then be rolled back to the last version before the attack by using the stored snapshots.
There is near-instant disaster recovery, we’re told. Any edge filer which has accessed the affected files has the folder containing the files populated nearly instantly with stubs that enable users to regain access to the recovered files on their mapped network drives. There is no need to wait for all the damaged data to be restored, CTERA says.
The dashboard can then be used for post-attack forensic activity.
By detecting attacks as they occur, using anomalous file IO activity, CTERA is not relying on existing ransomware attack signature patterns and claims it provides protection against zero-day attacks, which have no recorded signature.
Competitor Nasuni announced its inline Ransomware Protection service with attack detection feature in May last year, and claims it offers granular recovery down to one minute.
Panzura has immutable snapshot-based recovery for ransomware attacks but no real-time attack detection facility yet. Egnyte similarly has ransomware attack recovery features but no attack detection in real time.
CTERA Ransom Protect will be available for all CTERA Edge Filer customers in July. They get single click feature activation with this forthcoming software release.








