Nebulon hopes to give servers a personal anti-ransomware encryption security guard with its TripLine technology.
The hardware heart of Nebulon’s offering is a server-attached card, the services processing unit (SPU). The SPU is managed by Nebulon ON, a SaaS offering with three aspects: smartEdge to manage edge sites as a fleet; smartIaaS; and smartCore to turn a VMware infrastructure into a hyperscale private cloud.
It’s adding smartDefence to that mix – to detect encrypting ransomware attacks on servers, and recover the server to a point in time just before the attack using golden master software.

CEO Siamak Nazari said ransomware defences needed to be comprehensive. They should “cover the entirety of an organization’s infrastructure, and there are woefully few options to protect the server-storage infrastructure.” The AI-enhanced TripLine technology and associated TimeJump restore functionality and protect servers and their storage from ransomware attacks in a new way, according to Nazari. “CISOs and CIOs should demand such capabilities be an inherent part of any modern infrastructure deployment.”
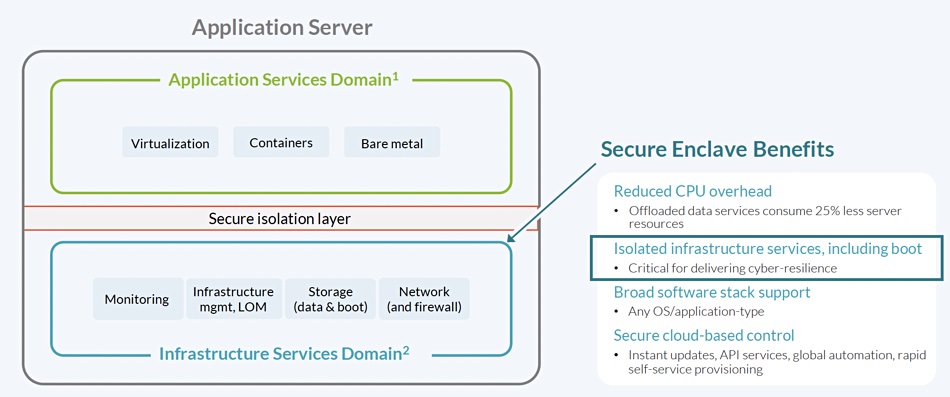
TripLine software is part of a secure enclave on a server fitted with the SPU. This concept was inspired by similar preventative boundaries set up by the cloud hyperscalers around their servers – think AWS Nitro Enclave. This enclave includes server lights-out management, data services, boot and data volumes, and attached SSDs, and is connected to the Nebulon ON cloud control plane.
The SPU’s software runs a machine learning model which monitors block-level I/O to storage drives. It can identify encrypted data blocks among the stream going to storage volumes and sends a count of them and the ratio of encrypted to unencrypted I/Os to the Nebulon ON cloud every 30 seconds. This cloud facility uses its own ML model and statistics to check the historical average of encrypted blocks for a given volume. If it finds five encrypted block count surges in a row for a volume, it will alert the customer about a potential ongoing encrypting ransomware attack.
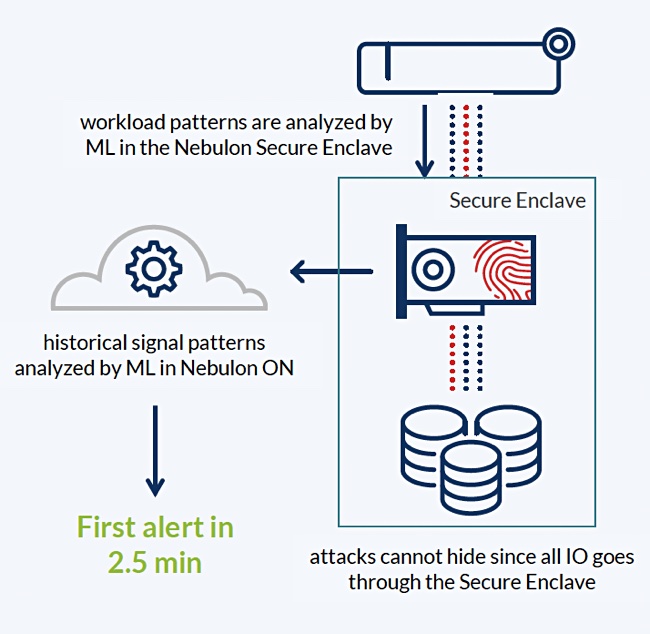
Because Nebulon ON is involved, it can share learned patterns across all connected systems and customers.

COO Craig Nunnes told us: “In conjunction we’ll use TimeJump, which is a very quick recovery of that whole software stack. You can very quickly ring fence where the attack is happening, reboot the server to eliminate the attack and and get on with it.” The attack’s blast surface is limited by this detection and response.
TripLine software protects stored application data and software and the operating system. Nunes claimed: “If you’re attacking the operating system binaries, if you’re trying to get to the the boot volume to execute some bit of code, we’re going to catch it.”
Nebulo says Hyperconverged Infrastructure (HCI) provides no isolation between infrastructure services and application services, and is particularly vulnerable to cyberattacks. When the HCI operating system becomes infected, data services become unavailable and the disks that store snapshots protecting application data become compromised, making fast recovery impossible.
Its SPU-based infrastructure contains master copies of a server’s software, enabling a clean reboot using uncompromized code. Nebulon calls this known good version of the operating system and application stack its ImmutableBoot, and it is stored in the server’s secure enclave.
Nebulon has set up a smartDefence ransomware detection and recovery offering which relies on TripLine and TimeJump. The inclusion of TripLine means customers can identify the precise point of attack within their infrastructure and revert to a secure state using TimeJump. This provides, Nebulon says, faster threat detection and response and a faster recovery than traditional reinstallation of server software.
Exfiltrating ransomware
We asked about Nebulon combating ransomware attacks that exfiltrate data – which would leave no suspicious encrypted data I/Os. Nunes said: “We would again rely on our machine learning technology. We would train it the way we’ve done this, as we’ve trained the technology in the cloud and deployed the model to the secure enclave, we would have to do something similar.
“The thing we have to look at is exfiltration is going to be a sequential stream, right? And there’s a lot of workloads that kind of look like that – your backup is going to look like that. And so we’re going to have to do some real serious machine learning work to determine is that just a backup or some other normal stream? Or is it something headed off site? It’s a high bar for our engineers to tackle, but they’re up for it.”
There was no commitment to a product offering, but we think Nebulon is researching this area intensively to see what it can develop.







