SaaS backup supplier Druva is making recovery from a ransomware attack faster by automatically identifying the latest clean backup before an attack — creating a single golden snapshot master as a recovery point.
It has announced Curated Recovery software technology, which checks backups to find the latest uncorrupted copy of files and places them in a so-called golden master snapshot — a clean recovery point.
Druva’s founder and CEO, Jaspreet Singh, said in an announcement quote: “Being the victim of a ransomware attack doesn’t need to be a choice between paying an exorbitant ransom or halting operations while IT teams go through an intensive, manual recovery process. … With our newest capabilities, every customer can gain the peace of mind of restoring their data with confidence.”
The company says a ransomware attack can start by silently infecting backup files two months or more before production data is attacked. This makes attack recovery much harder because restoring an infected backup can reintroduce the malware as well as having corrupted data restored. IT admin staff can spend days if not weeks searching for uncorrupted copies of data, and Druva’s Curated Recovery technology does this automatically.
It checks backups looking for ransomware and other malware signatures and anomalous activities, within a specified timeframe. Druva says the software then “builds an uncorrupted, unencrypted and malware-free recovery point to ensure a successful recovery before it’s ever initiated.” GigaOM analyst Alastair Cooke calls this “a synthetic restore point of the last known good file versions.”
Having a golden master to hand shortens the ransomware attack recovery time and can obviate any need to pay a ransom fee.
Curated Recovery is a new part of what Druva calls its Accelerated Ransomware Recovery module. This is a set of capabilities providing ransomware attack help:
- Access Insights Understand location and identity for all access attempts to gain situational awareness;
- Anomaly Detection Gain data-level insights on file changes, creation, recovery, and deletion — users can create alerts for anomalous activity and use anomaly information to identify the timeframe of an attack;
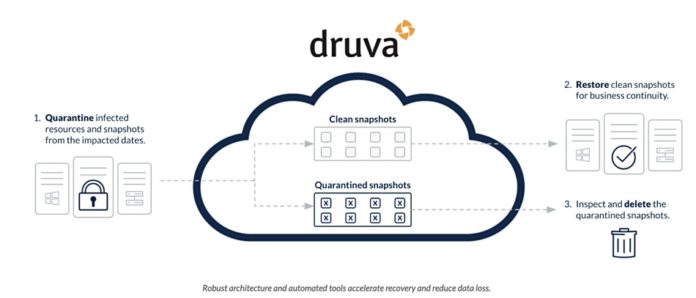
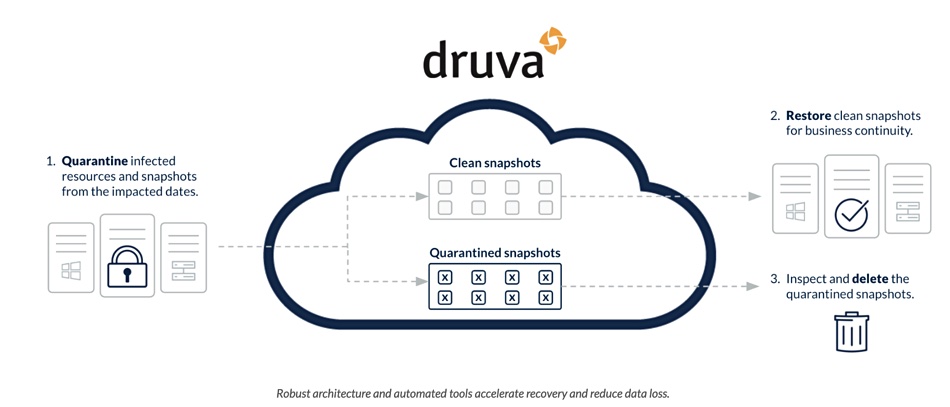
- Quarantine Quarantine infected systems and snapshots;
- Recovery Scans Scan snapshots for known malware and customer-provided indicators of compromise before restoring to avoid reinfection
Curated Recovery is now added to this list.
Read a Druva Solution Brief to find out more. The company’s blog web site will have a Curated Recovery blog posted to it shortly and a demo video will be made available as well.