Kaseya’s VSA remote monitoring and management tool was used as an attack vector to inject ransomware into the systems of fewer than 1,500 end-customers of some 30 managed service providers (MSPs) at the start of the USA’s Independence Day weekend.
Update: 6 July 2021. Updated numbers of affected customers added. More affected customers identified.
A Kaseya statement explained: “Kaseya’s VSA product has unfortunately been the victim of a sophisticated cyberattack. Due to our teams’ fast response, we believe that this has been localised to a very small number of on-premises customers only.“
VSA, the Virtual System/Server Administrator, is software used by Kaseya customers to monitor and manage their infrastructure. It is supplied either as a hosted cloud service by Kaseya, or via on-premises VSA servers. These SaaS VSA servers can be deployed by end-users or by MSPs. Kaseya sends out updates to these VSA servers and, on Friday July 2, an update was distributed that contained REvil ransomware code. It affected fewer than 60 Kaseya VSA customers — but around 30 of them were MSPs, and the code was then sent on to their customers. Potentially thousands of MSP client businesses were infected.
This is known as supply chain attack, and is similar in its basic methodology to last year’s SolarWinds attack, with malware installed via an update server.
Kaseya response
Kaseya has been putting out regular updates about the attack and its ongoing response efforts. It has turned off its own hosted and also SaaS VSA servers, and states emphatically that customers should turn off their own VSA servers until further notice.
A Kaseya statement on July 4 said: “Our security, support R&D, communications, and customer teams continue to work around the clock in all geographies through the weekend to resolve the issue and restore our customers to service.”
Customers who receive a ransomware demand should not click on links in the message, as the links may themselves be weaponised. How they should actually respond to the ransomware demand is not spelled out. Meanwhile, they could well find that some of their files are encrypted and will need to recover their contents somehow.
Kaseya advised: “We are in the process of formulating a staged return to service of our SaaS server farms with restricted functionality and a higher security posture (estimated in the next 24–48 hours but that is subject to change) on a geographic basis. More details on both the limitations, security posture changes, and time frame will be in the next communique later today.”

Kaseya is working with the FBI, the US Cybersecurity and Infrastructure Security Agency (CISA) and cybersecurity forensics firms, and its executives are contacting affected customers. The company’s R&D engineers are diagnosing the incident breach point and investigating how the attack code has affected customers. A Compromise Detection Tool was rolled out late on June 3 to almost 900 Kaseya customers who had requested it, and an update to this developing tool has also been distributed.
The tool can be used to find out if a customer’s VSA server has been infected. Some 2,000 Kaseya customers have downloaded the tool as of July 6.
It is developing a patch that will need to be installed prior to customers restarting their VSA servers, along with a set of recommendations on how to strengthen their security posture.
Attack vector and scope
Kaseya’s own systems were breached through a vulnerability that it became aware of from the Dutch Institute for Vulnerability Disclosure (DIVD) only recently, and which it was in the process of fixing. A DIVD statement on July 3 said: “We discovered severe vulnerabilities in Kaseya VSA and reported them to Kaseya, with whom we have been in regular contact since then.” The date that DIVD reported the vulnerability to Kaseya is not revealed.
Security firm Huntress Labs is updating a Reddit thread on the incident. It contains details of the initial intrusion into customers’ Kaseya VSA servers:
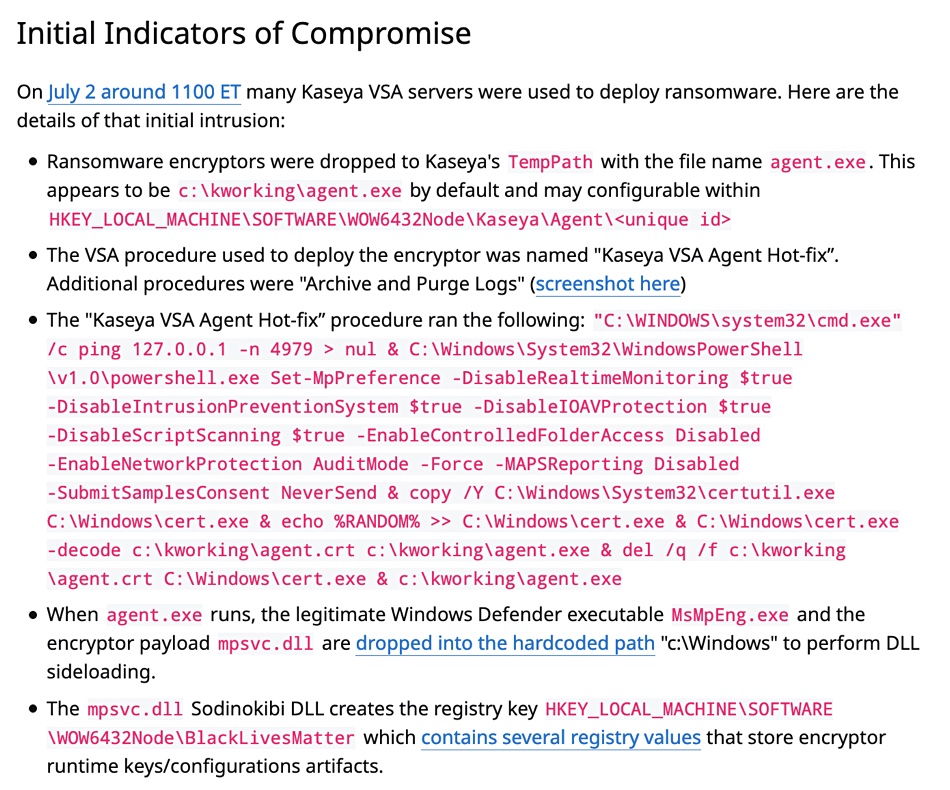
The thread includes these points:
- More than 1000 businesses had servers and workstations encrypted.
- It’s reasonable to think this could potentially be impacting thousands of small businesses.
- Based on the forensic patterns, ransomware notes and the TOR URL, we strongly believe a REvil/Sodinokibi RaaS affiliate is behind these intrusions.
Huntress believes that the cybercriminals exploited a SQLi vulnerability and that an authentication bypass was used to gain access into the VSA servers.
Sophos malware analyst Per Mark Loman is reported to have said that companies who have been impacted are seeing ransom notes of $50,000 or $5 million if their system is part of a larger corporate network.
According to The Record, Kaseya has been targeted twice before. “In February 2019, the Gandcrab ransomware gang abused a vulnerability in a Kaseya plugin for the ConnectWise Manage software to deploy ransomware on the networks of MSPs’ customer networks.”
The Gandcrab gang rebranded as REvil and then mounted a second attack against Webroot SecureAnywhere and Kaseya VSA products trying to get entry through them to MSPs’ customer networks.
In this latest attack the REvil code apparently tries to disable any local anti-virus code and then executes a phony Windows Defender application. This app runs the ransomware routines to encrypt files in the system.
Number of affected customers
Huntress Labs researcher John Hammond thinks there are more than 1000 affected businesses. (Hammond is tweeting about the incident.) These are located around the globe including in Argentina, Canada, Germany, Kenya, Mexico, The Netherlands, New Zealand, South Africa, Sweden, the UK and the USA and other countries..
Kaseya has since said fewer than 1,500 end-customers were affected.
Bloomberg reported that Synnex Corp. and Avtex LLC are two affected US MSPs. New Zealand Kaseya-using MSP Datacom shut down its servers. An un-named German ISP was hit. Dutch ISPs VelzArt and Hoppenbrouwer Techniek are reported to have been affected.

An 800-branch Swedish grocery chain, the Coop, had its point-of-sale terminals disabled because the actual payment code service came from a Swedish MSP called Visma Esscomn. This is a Kaseya customer with a million customers, according to its press notice about the incident. It distributed the ransomware code to the Coop’s checkout terminals and they could no longer accept payments.
The Coop initially closed all 800 stores, then set about recovery work. Its customers can use a Coop mobile phone Scan & Pay app in some stores.
Sweden’s State Railway organisation was also hit, as was a Swedish pharmaceutical chain.
Comment
This disgusting cyber-piracy seems unstoppable. The only effective defence for victims would seem to be recovery from immutable backups, preferably with granular point in time recovery and fast restores so that data loss is minimised.
It is ironic that Kaseya offers its own Unitrends backup, which has an anti-ransomware capability. Even more ironically, it also provides a Managed SOC service that provides 24/7 threat monitoring with this pitch: “Stop attackers in their tracks with our managed cybersecurity detection and response solution backed by a world-class security operations centre.”
US president Joe Biden met Russia’s President Putin in Geneva in June and told him that the USA would hold Russia accountable for cyberattacks against US companies and organisations if the attacks originated in Russia. He is reported to have directed intelligence agencies in the USA to investigate the attack.
If a Russian origin to the Kaseya incident is identified, exactly how Russia would be held accountable is not specified. Meanwhile a thousand-plus businesses around the globe are having their data held to ransom because Kaseya was the unwitting agent used to ship ransomware to their systems.
Future legal actions may try to get Kaseya to pay compensation to affected businesses. The amount of lost business by Sweden’s Coop could run into millions of kronor. Kaseya’s fast and constantly updated response to the attack will help mitigate reputational damage, but the consequential financial cost could be literally enormous.








