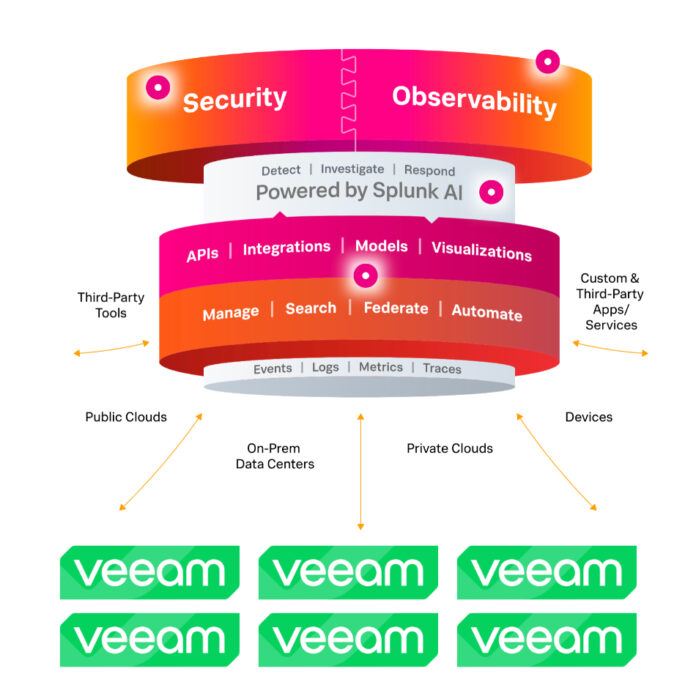
Veeam has set up a connector so customers using Splunk to monitor their IT infrastructure can monitor Veeam Backup and get alerts about issues.
Cisco-owned Splunk captures, stores, indexes and correlates real-time, machine-generated IT infrastructure data from multiple sources. Users can access Splunk dashboards to monitor their infrastructure and handle issues. Splunk says it counts 92 of the Fortune 500 companies as customers for its security information and event management (SIEM) software. Veeam has more than half a million customers for its backup and restore product, and its larger enterprise customers are also likely to be Splunk customers. The Veeam App for Splunk adds Veeam as a data source.

CRO John Jester said in a statement: “Veeam is focused on powering data resilience for every customer and this includes tight integration with the leading security platforms.”
The app integrates with Splunk user roles and location management. It processes events sent by Veeam Backup & Replication to the syslog server and provides Splunk users with the following features:
- Built-in dashboards to monitor job statuses and security events on a daily basis
- Built-in reports and alerts
- Severity level management for events and alerts
- Multiple Veeam Backup & Replication servers support
- Multiple data source locations support
- Role-based permissions for locations
- App configuration backup
Jester said: “Security professionals can use Splunk to closely monitor their Veeam backup environments through detailed dashboards, reports and alerts. Combating cyberattacks requires integration across your infrastructure, and the Veeam App for Splunk brings Veeam event data into Splunk, enabling customers to monitor security events like ransomware, accidental deletion, malware and other cyber threats using their current tools.”
Veeam ONE v12.1 introduced Syslog SIEM integration. Enterprises will generally prefer to have a single SIEM facility and not have to check individual applications, like Veeam ONE, for their security status and activities. Jester recognized this, saying: “It means enterprises can quickly and easily process vital monitoring and event data on their Veeam backup environments, in the same single pane of glass as other source environments they may be monitoring.”
Veeam is steadily becoming more enterprise friendly. With this Splunk connector, it is following in the footsteps of competitors Cohesity, Commvault, Druva, Rubrik and Veritas who already have Splunk integrations. Veeam can already be integrated with Graylog, IBM’s QRadar, Micro Focus ArcSight, LogRhythm and AlienVault by having Veeam send syslog data, SNMP traps and other log data to the SIEM product. The Splunk App is a step forward on Veeam’s SIEM integration path.
Veeam App for Splunk supports Splunk Enterprise 9.1.0 and later and Splunk Cloud Platform 9.1.2308 and later, and is available now via Splunkbase here. Veeam App for Splunk is free with a Veeam Data Platform Advanced or Premium license that includes syslog event forwarding support.