Asigra has released Tigris – a data protection software product – aimed at detecting and disarming malicious code embedded deep within zipped content files, where it is invisible to most scanners.
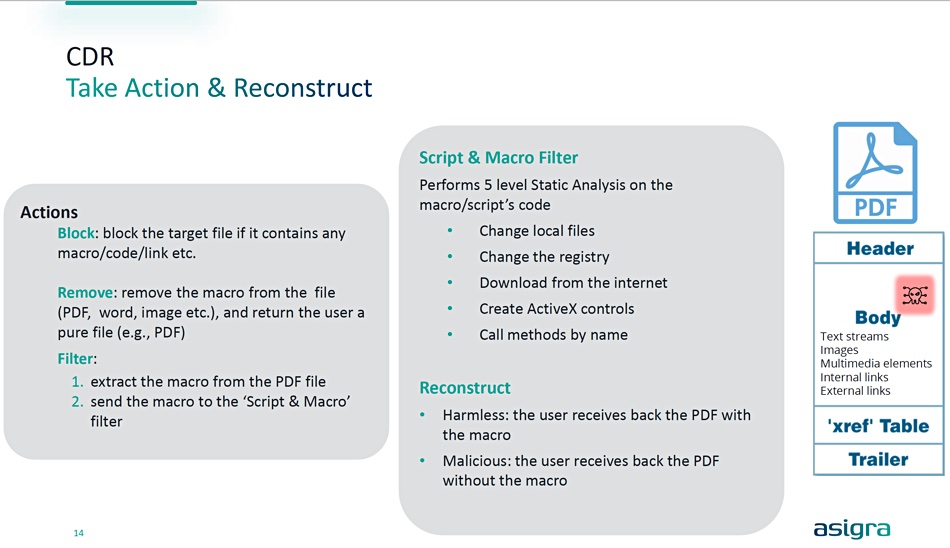
Headquartered in Toronto, Asigra and has a variety of data protection offerings covering endpoints, datacenters, and SaaS services available worldwide. Tigris Backup, formerly called Asigra Cloud Backup, is agentless. Tigris Data Protection software with CDR (Content Disarm & Reconstruction) looks inside nested or zipped files to seek out embedded malware code, malicious macros, scripts, links or executables. It removes any detected malware and then reconstructs the file.
Asigra CTO Val Silva issued a statement saying ransomware attacks “are commonly finding their way within corporate networks, and in many cases, specifically targeting backup systems. With Asigra CDR, Tigris Data Protection has reset the bar with ultra-secure backup that ensures organizations meet their business continuity objectives for absolute confidence in the ability to recover mission critical data when needed.”
The company says its CDR tech includes:
- Breaking down each archive/file into its smallest components
- Backup/recovery stream scans each component for potentially embedded malicious or unauthorized content – macros, scripts, etc.
- Flexible operation with user-defined policies (filter, block and remove) to act on potentially dangerous objects
- Inline scanning with the ability to break down each archive/file into its smallest components, cleanse the data and re-constitute in-stream as clean, recoverable data
- Bi-directional scanning, allowing CDR scanning of all files prior to encryption and delivery to the backup repository, as well as CDR scanning during recovery, prior to the files re-entering the production network
Tigris CDR will remove the macro, link, executable, etc. from the scanned file (PDF, word, image etc.) and return a pure file (e.g. PDF) to the user, says Asigra.
Tigris’ capabilities include zero-day exploit protection, Deep MFA (multi-factor authentication), variable repository naming to non-standard names to prevent recognition and encryption/deletion and FIPS 140-2 certified encryption. It can also do a soft delete; moving the malware data to a hidden folder for a set period of time pre-determined by the admin, and so deceiving the malware into thinking it has eliminated the backups.








