NexiTech has taken the security idea of frequency-hopping radio systems and applied it to storage drive IO – such that its software hops between drive types to obstruct malware attacks.
The background is a military one. Static targets are easier to attack than dynamic, moving targets. This applies to military personnel and equipment, like tanks, and also military signalling systems, such as wireless, hence frequency hopping to obstruct wireless channel eavesdropping. Nextech’s software treats a drive type as an I/O channel and randomly hops between them so that an attacker expecting I/O to a storage drive with a file system actually sees the write channel changing to a tape target system, then an SSD, then iSCSI-accessed disk drive, a SATA SSD, and even make-believe drive types and decoy honeypot drives.
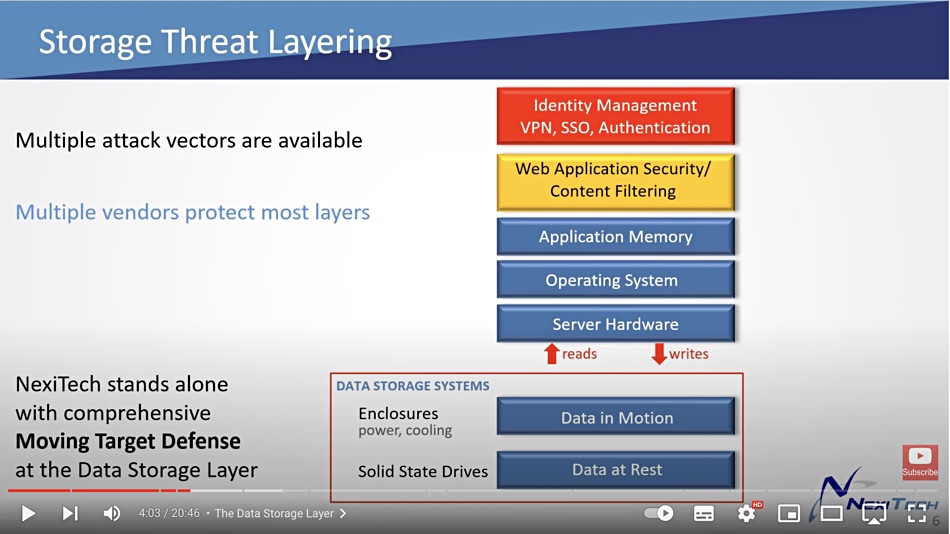
Nextech’s software maps the apparent, externally-visible drive type to the actual drive type during these random changes so that the legitimate internal I/Os complete as normal.
Founder and CEO Don Matthews presented this concept in a YouTube video in which he talked about the origin of his software. “Our first commercial product was a software interface layer that basically translated one storage related api into another. In the early days of Windows Microsoft included a particular type of storage API called ASPI (Advanced SCSI Programming Interface) and many vendors implemented application programs that used this interface including the US Air Force.”
“In later versions of Windows Microsoft dropped that API in favor of a different one that they came up with, and so it was necessary to translate between the old one and the new one in order to provide backwards compatibility for those folks that had created applications that used the old API.”

There was an internal Windows access security obstacle, but: “We found a way around … security restrictions from Microsoft and that means that we can now send any storage related command we like to any storage device. That’s a pretty powerful capability. If we can figure out how to do that someone else probably can too.”
Its software implements an AMTD (Automated Moving Target Defense) capability. The AMTD idea is discussed and explained in a 25-page Gartner report which also looks at suppliers.
This is how Matthews explains Nextech’s AMTD capability: “At its core we use storage virtualization to create multiple abstractions of a device. We also change the device type. We have the capability to emulate any type of device we want so we could, for instance, take a disk device and make it look like a tape device or make it look like an unknown device.”
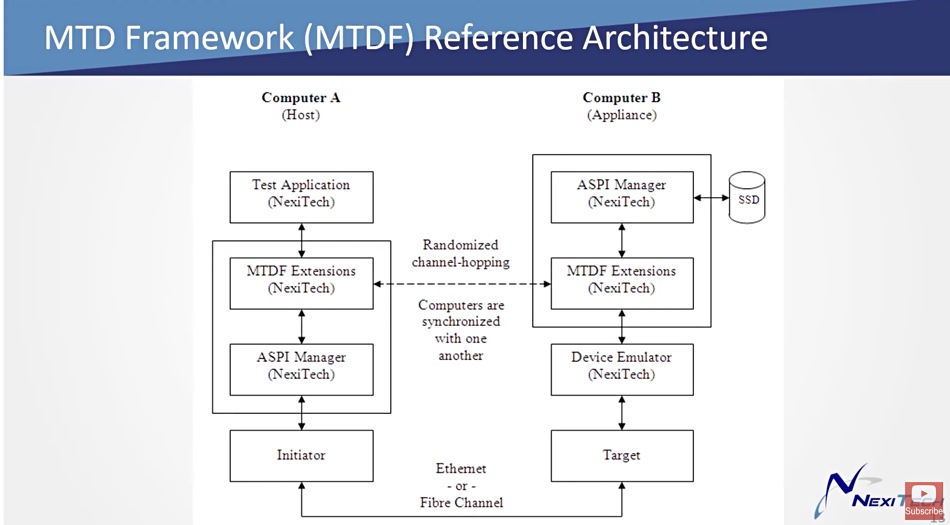
“So we’ve cloaked the device by changing its device type. The host operating system now has no idea how to talk to this thing because it’s no longer a disk drive. This alone is an effective ransomware protection by the way, because most ransomware attacks depend on the fact that there is a usable file system on the disk device. No file system, no ransomware attack.“








