A GigaOm report looking at ransomware protection facilities supplied by file storage vendors puts RackTop in the lead followed by Cohesity and Nutanix.
Seventeen suppliers are examined in GigaOm’s Sonar Report for File-Based Primary Storage Ransomware Protection. This document looks at these suppliers and includes a forward-looking analysis of their products in terms of ransomware protection. Each vendor is assessed on its innovation and architecture approach, and where it sits in terms of enabling rapid time to value (Feature Play) versus delivering a complex and robust system (Platform Play).
Senior GigaOm analyst Enrico Signoretti said: “RackTop provides a no-compromise approach to ransomware protection with a strong zero-trust foundation and a feature set that will continue to deliver long-term value to organizations.”
The report summary says that, although dedicated out-of-band ransomware protection solutions exist, organizations should not underestimate the benefits of in-band ransomware protection capabilities embedded in NAS solutions. The most effective mitigations include a combination of in-band and out-of-band capabilities, but for smaller businesses or cost-conscious organizations, NAS ransomware protection solutions constitute an important first line of defense.
NAS systems are prone to ransomware attacks because they present all the characteristics that facilitate a ransomware attack, including:
- Primary point of storage for collaboration use cases broadly used by human operators within the organization
- Primary storage target for many data asset types, regardless of their criticality
- Shared storage, usually accessible by numerous individuals across many geographic locations
- Broad range of types and large numbers of files accessible by many individuals, therefore accessible by any malicious process running on their endpoints
- Lax or nonexistent permissions on certain shares and folders
Without proper controls (for example, segmentation of data, least-privilege access, and stringent permissions), file storage repositories become easy targets for the uncontrolled spread of ransomware.
Immutable snapshots provide the most basic level of protection. Combining them with other techniques, such as replication, provides an intermediary level of protection. The most advanced implementations provide sophisticated ransomware identification algorithms trained using artificial intelligence and machine learning (AI/ML) models.
A report chart plots the current position of each vendor against feature play, platform play, and innovation radial axes across a field of two concentric semicircles, with suppliers (and their products) set closer to the center judged to be of higher overall value. The outer circle is for Challengers with the inner one being for Leaders. Vendor progress is indicated by blue arrows that show the expected direction of movement over 12 to 18 months. Faster-moving vendors have black arrows.
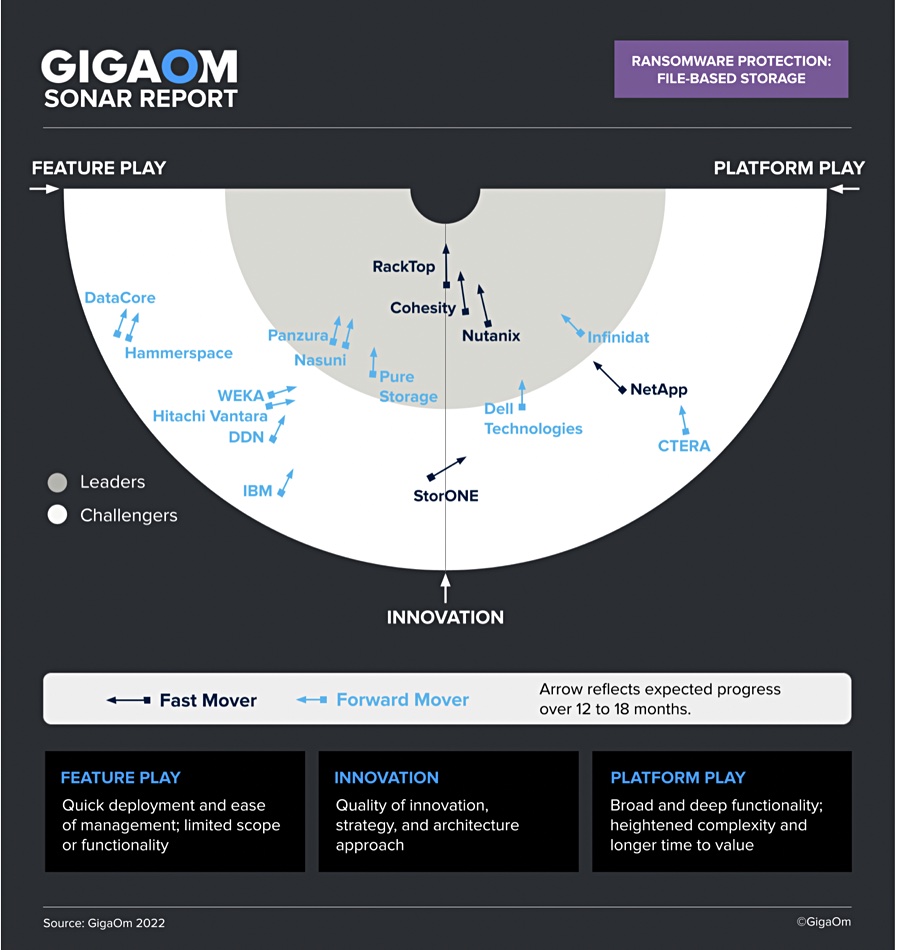
The other leaders are, in alphabetic order, Infinidat, Nasuni, Panzura, and Pure Storage. We have a group of six suppliers in the Feature Play part of the Challengers semicircle, and Dell, NetApp and CTERA in the Platform Play part. NetApp is moving quickly towards the Leaders area. StorONE is in the middle of the Challengers semicircle and moving into the Platform Play area.
File storage supplier VAST Data is not included in the report. Its VASTOS v4 software includes indestructible and immutable snapshots as a safeguard against ransomware attacks. HPC file storage supplier Panasas is another absent vendor.
The ransomware-repelling properties of public cloud file storage offerings are also not examined in the report.
The full GigaOm document, with measurement criteria, vendor scores and vendor descriptions, can be downloaded here.








