Dell Technologies Capital has invested in Calamu, an anti-ransomware startup with so-called safe harbour technology.

Calamu was founded this year by CEO Paul Lewis and has offices in San Jose and Clinton, New Jersey. It raised $2.4 million in a seed round in April and has just announced the participation of Dell Technologies Capital.
Raman Khanna, Managing Director, Dell Technologies Capital, issued a canned quote: “Calamu has the potential to revolutionise how enterprise data is stored, managed, and secured. Their unique data protection technology brings a powerful solution to the ongoing fight against ransomware and other cybersecurity threats.”
Calamu’s Protect “safe harbour” technology hashes, compresses, encrypts data, and then breaks it up into three fragments with redundancy. Then it re-encrypts them and stores them in in three separate locations, using different public clouds — AWS, Azure and the Google Cloud Platform — or local file systems. Authorised users can access the data in the normal way. When they do, the data is decrypted and reassembled by the Calamu Protect software.
Clearly this makes data access times longer than, for example, reading an entire data item from a local SSD. Calamu claims that its advanced compression and patented processing ensures no “significant” performance impact.
In theory, an attacker would need to combine the three fragments to reconstitute the data and then steal a copy.
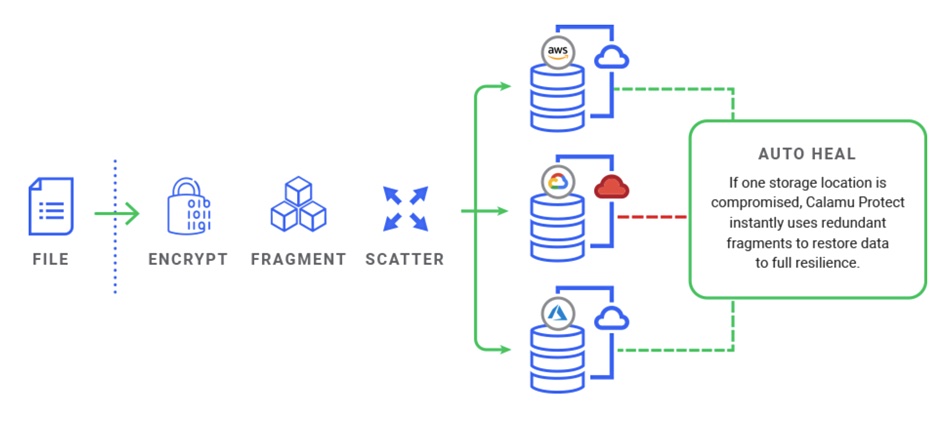
Protect monitors data integrity and can detect a ransomware attack, auto-healing data after a breach is detected. When a breach or outage is detected in one location, that location is sequestered, and the Protect software uses the two other fragments and their built-in redundancy to restore the data to its full state in real time.
Any attacker that gets access to single fragments cannot reconstitute the whole data items.
Calamu says Protect doesn’t store a complete file in any one location, giving customers full control over who can view their data — even if subpoenaed. That means it cannot be surreptitiously acquired by US law enforcement or intelligence agencies. Calamu’s technology can also be used to securely and privately transfer data between two parties while supporting overall compliance. Data protected by Calamu is compliant with many data privacy regulations.
In effect, Calamu’d data ceases to exist in readable form anywhere, unless accessed through Protect. How is that done? Calamu says data is accessible to the rightful owner, using either a GUI or, for application access, an API. But how is the identity of the rightful owner established? It’s publicly-available information resources don’t say.
Clearly, if a phishing attack gives an attacker the credentials of a rightful user then a Calamu data store could be accessed, the data copied, and encrypted before being written back. A phishing attack giving partial access to the Calamu data store would be thwarted though.
Calamu technology could possibly be able to detect the access pattern of ransomware attack activity, and its monitoring of data integrity implies that it may be able to do so. But there is no information yet available about how this would be done. This is not unexpected — Calamu is after all a very young company in its seed round period.
Read an information sheet to find out a little more.








