Azure blob storage has been used in phishing attempts, with Microsoft-issued domain and SSL certification that makes the bait seem credible.
The exploit involves a PDF decoy document purported to belong to a Denver, CO law firm and hosted in Google Drive. This contained a link to an Office 365 phishing page hosted in Azure blob storage.
Netskope, a cloud security vendor which uncovered the attack, detected the PDF decoy docs as PDF_PHISH.Gen1. It was described in a host email as “Scanned Document… Please Review.pdf” – such things traditionally arrive as email attachments sent to victims.
Upon clicking the link, victims were given a ‘Download PDF’ button. Clicking on that button generates a message about downloading an Azure Blob storage document – https://onedriveunbound80343[.]blob.core.windows.net – with a clickable hyperlink:
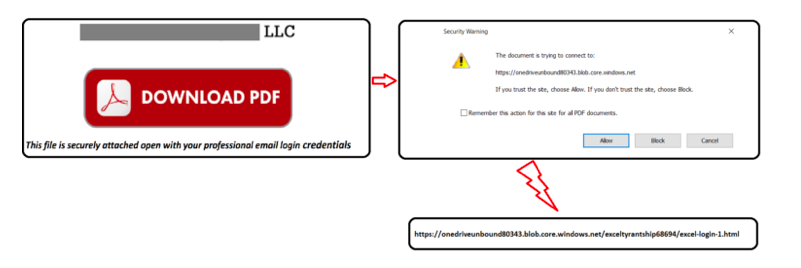
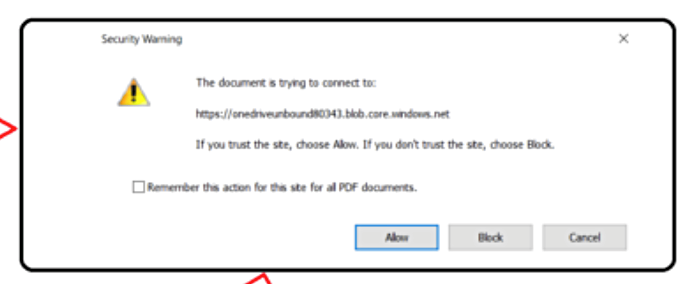
Clicking that leads the victim to a log-in screen asking them to sign in with their valid Office 365 email account. After some to-and-fro the victim is directed to a download page but nothing is actually downloaded.
Netskope found a similar phishing attack purporting to be from an Oregon-based dental equipment manufacturer. The company says this attack appears to be broadly targeted toward Office 365 users in the US.
How can users defend themselves?
Netskope says “The phishing bait was a Microsoft Office 365 login page, hosted on a Microsoft domain, with a valid Microsoft-issued certificate. Users can recognize that this is a phishing site based on the subdomain, which indicates that it is in Azure blob storage, and not an official Microsoft website. “
It recommends: “Enterprises should educate their users to recognize AWS, Azure, and GCP object store URLs, so they can discern phishing sites from official sites. “
In particular: “Always check the domain of the link. Know the domains typically used when you login to sensitive services. Additionally, be able to identify common object store domains, such as those used by Azure blob storage. This knowledge will help you differentiate between well-crafted phishing sites and official sites.”
Vice advice
It’s a Wild West phishing nightmare out there. But it unrealistic to ask unreliable potential victims to manually check the domain of links. It is also unfeasible to teach users to doubt the reliability of Microsoft-issued domain and SSL certification. What is the point of these certifications if they can be effectively counterfeited?
The Netskopers say: “Get comprehensive threat and malware detection for IaaS, SaaS, PaaS, and the web with real-time, multi-layered threat detection and remediation to prevent your organization from unknowingly spreading similar threats.”
Yes indeed. Or do not click on hyperlinks in emails unless you are certain it’s safe to do so.








